Back to basics - DNS, DHCP, and the Default Gateway in Enterprise Networks
Dynamic Host Configuration Protocol (DHCP): Purpose and Operation

DHCP Overview: DHCP is a network protocol that automates IP configuration for hosts. Instead of manually assigning IP addresses, subnet masks, default gateways, and DNS servers to each device, a DHCP server centrally manages these settings and leases them to clients on demand[1]. DHCP operates at the application layer and uses a client-server model: a new client (DHCP client) requests config data, and a DHCP server responds with appropriate network parameters (IP address, mask, gateway, DNS, etc.)[1]. This automatic process reduces configuration errors and IP conflicts and simplifies administration in large networks[2][3]. DHCP Lease Process (DORA): The DHCP client lease acquisition involves a four-step DORA handshake[4]:
- Discover: When a new host connects, it broadcasts a DHCPDISCOVER message (UDP source port 68, destination 67) to find any DHCP servers[5][6]. Because the client has no IP yet, this discover is sent to the local subnet’s broadcast address (255.255.255.255) so that any server on that network can respond.
- Offer: A DHCP server that receives the discover will reserve an available IP from its scope (address pool) and reply with a DHCPOFFER message. The offer contains the proposed IP address and other network settings (such as subnet mask, default gateway, DNS servers)[7][8]. The offer is often sent via unicast to the requesting client’s MAC (if supported), or broadcast if the client can’t yet receive unicasts[9].
- Request: Upon receiving an offer, the client typically accepts one (if multiple offers received) and broadcasts a DHCPREQUEST message identifying the server and lease it’s accepting[4]. This lets all DHCP servers know which offer was taken so only the chosen server proceeds[10][11]. The request message also serves as a renewal if sent later (it’s used both for initial lease and renewals).
- Acknowledgment: The selected server finalizes the exchange with a DHCPACK message, confirming the IP lease and providing the final settings. At this point, the client configures its network interface with the provided IP configuration and can use the network[4]. (If a server must deny the request, e.g. due to conflict, it would send a DHCPNAK.)
This DORA process occurs quickly and establishes a “lease”, the client is allowed to use the IP for a length of time (the lease duration). DHCP uses UDP ports 67 (server) and 68 (client) for these exchanges[12]. After a lease is granted, clients typically renew it by sending a new request at half the lease time (T1 timer) to keep the same address[13]. If the DHCP server is unreachable when renewing, the client will retry and eventually broadcast to any available DHCP server (rebinding)[14]. This ensures resilience, if the original server is down, another server (if configured for the subnet) could extend or reissue a lease[14].
Scopes and Configuration: A DHCP scope (or pool) is the range of IP addresses the server is authorized to assign on a particular subnet. For each scope, the administrator defines the network ID and subnet mask and often excludes certain addresses from dynamic assignment (e.g. the router’s IP, servers’ IPs) to avoid conflicts[15][16]. For example, if a subnet is 192.168.0.0/24, the DHCP scope might cover 192.168.0.51–192.168.0.254, excluding .1–.50 which are reserved for the default gateway and static devices[16][17]. The DHCP server will then hand out addresses in the allowed range and track active leases. It also manages lease expiration and reuse: when a lease expires and is not renewed, that IP returns to the free pool for others.
DHCP Options (Gateway, DNS, etc.): Beyond IP addresses, DHCP provides options to deliver other network configuration settings to clients[1][18]. Common DHCP options in enterprise networks include:
- Subnet Mask (option 1): The mask for the assigned IP’s subnet.
- Default Gateway (option 3, “router”): The IP address of the router that the client should use to reach other networks[18]. This is critical, it tells the host how to send traffic to external networks (like the internet). Without a correct default gateway, a host can only communicate within its local subnet. Typically the gateway is a router interface IP on that subnet (e.g. 192.168.0.1) which the server supplies via DHCP[18].
- DNS Servers (option 6): The address(es) of DNS server(s) that the client should use for name resolution[19]. Usually two DNS server IPs are given (primary and secondary) for resilience.
- Domain Name (option 15): The local domain suffix (e.g. example.com) clients should append to unqualified names. In Windows enterprises this is often the Active Directory domain name.
- Other options: NTP time servers, WPAD proxy, DHCP vendor-specific info, etc., can be provided as needed. Enterprise DHCP servers commonly set at least the gateway and DNS options so that clients can route and resolve names immediately upon getting an address[20].
When configuring a DHCP server (e.g. Cisco IOS device or Windows Server), these options are set per scope. For instance, on a Cisco router one might create a DHCP pool and specify the network, default-router (gateway), dns-server, and lease time for that scope[21]. On Windows DHCP, similar settings are configured in the scope properties (Router, DNS, DNS Domain Name, etc.). The DHCP server includes those options in its DHCPOFFER and DHCPACK messages, so the client autoconfigures things like its gateway and DNS settings alongside the IP[7]. Lease Renewal and Rebinding: DHCP leases are time-limited. The client will typically attempt renewal at 50% of the lease duration (T1). This is a unicast DHCPREQUEST to the original DHCP server to extend the lease[13]. If that server responds with DHCPACK, the lease is renewed. If not (server down or unreachable), the client keeps trying. By 87.5% of lease time (T2), if still no response, the client rebinds by broadcasting a DHCPREQUEST that any available DHCP server can answer[14]. This allows a backup DHCP server to take over. If no renewal occurs by lease expiration, the client must drop the IP and start discovery again[22]. Administrators configure lease lengths based on network needs, e.g. a few hours on guest networks or days/weeks on stable LANs – balancing between address turnover and administrative overhead. DHCP in IPv6: It’s worth noting that IPv6 has a similar protocol DHCPv6, but it differs in that IPv6 hosts often learn the default gateway via ICMPv6 Router Advertisements (not via DHCP). DHCPv6 can still provide DNS server info and other options, and assign addresses if using stateful configuration[23]. However, the classic IPv4 DHCP (as described above) remains widely used in enterprise IPv4 networks.
Domain Name System (DNS): Purpose and Operation
DNS Overview: The Domain Name System (DNS) is the hierarchical, distributed naming system that translates human-friendly hostnames into IP addresses (and vice versa)[24][25]. This allows us to use easy names like www.google.com instead of having to remember 142.250.181.46[26]. DNS is essential for most network applications – for example, when you type a URL or use an email address, your system uses DNS to find the corresponding IP. In an enterprise, DNS also maps internal resources (servers, printers) to names and is tightly integrated with directory services (like Active Directory) for service discovery. DNS Hierarchy and Zones: DNS names are organized in a hierarchy of domains. At the top are the root servers (denoted by a dot “.”), which delegate to Top-Level Domains (TLDs) like .com, .org, .net, country TLDs, etc. Under TLDs are second-level domains (e.g. example.com), and further subdomains (e.g. host.sales.example.com). A DNS zone is an administratively managed portion of the namespace, for which an organization’s DNS servers are authoritative. For instance, a company might control example.com and run DNS servers authoritative for that zone, containing records like www.example.com -> IP. DNS is decentralized, each zone’s owners maintain their own DNS records, and root/TLD servers only tell resolvers where to find the authoritative servers for each domain[27][28]. Resource Records: DNS stores data in resource records (RRs). Different record types serve different purposes, the most common being:
- A record: Maps a hostname to an IPv4 address[29]. (e.g. www.example.com → 93.184.216.34).
- AAAA record: Maps a hostname to an IPv6 address[29].
- CNAME record: An alias for another name[30]. (e.g. ftp.example.com CNAME to server1.example.com).
- MX record: Mail exchanger – specifies the mail server for a domain[30].
- PTR record: Pointer record for reverse DNS – maps an IP address to a hostname[31]. (stored in special reverse lookup zones, e.g. 5.4.3.2.in-addr.arpa → host.example.com).
- NS record: Nameserver – indicates the authoritative DNS servers for a zone[32].
- SOA record: Start of Authority – contains zone metadata (primary server, admin email, serial number, etc.)[33].
- TXT record: Free-form text – often used for SPF, DKIM and other metadata[30].
- SRV record: Service locator – maps a service name to a host:port (used in AD, etc.)[33].
These records allow DNS to not only resolve hostnames to addresses but also support services like email routing (MX) and service discovery. Name Resolution Process: When a client needs to resolve a name, it uses a DNS resolver (usually part of the OS) to query a DNS server. Typically, the client’s stub resolver will send a recursive query to a configured DNS server (often a local corporate DNS or an ISP DNS). A recursive query means “give me the final answer or an error, but don’t send me somewhere else”. The DNS server (if configured for recursion) then becomes the DNS resolver for that query, taking on the task of finding the answer by querying other servers. This process often goes through multiple steps (an iterative resolution across the hierarchy):
- Recursive vs Iterative Queries: In a recursive query, the server contacted must do all the work to resolve the name and return the final answer; the client expects either a valid result or a failure[34]. In an iterative query, the server can reply with a referral to a different DNS server that is closer to the answer (e.g. “I don’t know this name, but try this server...”)[34]. Typically, end-client systems use recursive queries to their local DNS server, and that DNS server then uses iterative queries to navigate the DNS hierarchy on the client’s behalf[35].
How a Name is Resolved (example): Suppose a client in an enterprise network wants to resolve www.wikipedia.org. It will ask its configured DNS server (with a recursive query) “What is the IP of www.wikipedia.org?”, if that local DNS server doesn’t already know (not cached, not authoritative), it begins iterative resolution:
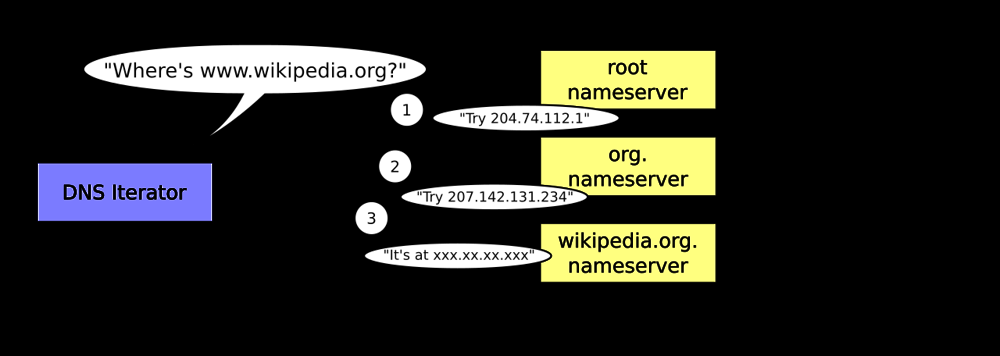
Illustration: A DNS resolver performing iterative queries. The resolver (left) asks the root nameserver, which refers it to an org TLD server, which then refers to wikipedia.org’s server, and finally gets the IP answer[28]
- The resolver queries a root nameserver: “Who knows www.wikipedia.org?” The root server doesn’t have the answer, but responds with a referral: “I don’t know, but the DNS servers for .org are at [IP addresses]. Try them.”[28]
- The resolver then queries one of the .org TLD nameservers: “Who knows www.wikipedia.org?” The TLD server responds: “I don’t have that host, but the wikipedia.org domain is served by these DNS servers...” , a referral to the authoritative DNS for wikipedia.org[28].
- The resolver then queries the wikipedia.org authoritative nameserver: “What’s the IP for www.wikipedia.org?” As the authoritative server, it responds with the final answer: “www.wikipedia.org = 192.0.2.123” (for example).
- The resolver returns this answer to the client that requested it[36].
All these steps are usually invisible to the end-user; it happens in milliseconds. The DNS server caches the referrals and answer so that subsequent lookups for the same name (or other names in wikipedia.org) can be answered more quickly from cache[37]. DNS caching is very important – it reduces latency and external queries. Each DNS record has a TTL (time-to-live) after which it expires from cache[38][39]. Local and Enterprise DNS: In an enterprise network, the DNS servers configured (via DHCP or static config) on clients are usually internal DNS servers (or forwarders) that can resolve both internal hostnames and external queries. For internal domains (e.g. an Active Directory domain like corp.example.com), the company’s DNS servers are authoritative. When resolving external names, the enterprise DNS servers often forward queries to a recursive resolver (ISP or cloud DNS) or perform recursion themselves out to the internet root/TLD servers. This may be subject to firewall rules, e.g., only the internal DNS can go out to the internet for DNS, clients must use internal DNS. DNS Query Transport: DNS typically uses UDP port 53 for queries and responses. UDP is fast and efficient for small queries. If a response is too large for UDP (over 512 bytes in classic DNS, though EDNS0 allows larger UDP packets), or for certain operations like zone transfers, DNS will switch to TCP port 53[40]. For example, a full zone transfer between DNS servers uses TCP. Administrators ensure that firewalls permit at least UDP/53 (and often TCP/53) between clients, DNS servers, and the internet as needed[40]. Recursive Resolvers and Root Hints: Enterprise DNS servers usually are configured with a root hints file (addresses of root servers) to start the iterative process, or they forward all unknown queries to an upstream resolver (like a ISP DNS or a filtering DNS service). In either case, the goal is to resolve names recursively for clients. Modern networks may use features like DNS over HTTPS/TLS for privacy, but the fundamental resolution process remains the same.
Reverse DNS: Enterprises also set up reverse DNS zones (e.g. for their IP ranges) so that IP addresses can be resolved back to hostnames (PTR records). This is useful for logging, security (some services do a PTR lookup on client IPs), and administration. Typically, an enterprise manages PTR records on their DNS for internal subnets, and coordinates with their ISP for public IP reverse DNS entries.
How DHCP and DNS Work Together in an Enterprise
DHCP and DNS are complementary: DHCP configures hosts with IP addresses and informs them of DNS servers, while DNS provides name-to-IP resolution for locating network resources. In an enterprise environment, they often interact closely to ensure that as devices come and go, name records stay updated and clients can find each other by name. Providing DNS Configuration via DHCP: The simplest interaction is that a DHCP server supplies the IP addresses of the organization’s DNS servers to clients as part of the lease (DHCP option 6)[19]. For example, when a laptop joins the network, DHCP not only gives it an IP but also tells it “Use 10.1.1.100 and 10.1.2.100 as your DNS servers.” The client’s OS will then send DNS queries to those servers. This automatic provisioning ensures all clients use the correct internal DNS (vital in Active Directory environments, where using an external DNS would fail to resolve internal hostnames). DHCP can also provide the DNS search domain (option 15) so that clients append the company domain to unqualified names. This way, a user can just ping “fileserver” and the system knows to resolve “fileserver.corp.example.com” via DNS. Dynamic DNS Updates: In a dynamic network, clients’ IP addresses (and even hostnames) can change frequently (due to DHCP lease churn, laptops moving, etc.). Dynamic DNS (DDNS) is a mechanism that allows DNS records to be updated automatically when such changes occur. Many enterprise setups enable DHCP and DNS to coordinate on updating DNS records for DHCP clients[41]. There are a couple of approaches:
- Client Updates: The DHCP client (i.e. the host machine) can itself send DNS update requests to the DNS server when it obtains a lease. For instance, a Windows PC by default will attempt to register an “A” record for its hostname pointing to its new IP, and possibly update its old record if the IP changed[42][43]. Likewise, it may attempt to register a PTR record for reverse lookup. This is done via DNS dynamic update protocol (RFC 2136) and typically requires the zone to allow updates from that client (in AD, secure updates tie into computer account permissions).
- DHCP Server Updates: Alternatively (or additionally), the DHCP server can perform the DNS update on behalf of the client. In Microsoft DHCP, for example, there’s an option to “Always dynamically update DNS A and PTR records” for DHCP clients, even if they do not request it[44][45]. When a lease is given to a client, the DHCP server will send an authenticated dynamic update to the DNS server: “Add/modify the A record for hostname X to IP Y, and the PTR for IP Y to hostname X.” This is especially useful for devices that may not themselves know how or be configured to do DDNS (like some IoT devices, VoIP phones, etc.).
In Active Directory environments, secure dynamic updates are used, only trusted DHCP servers (identified by credentials) or the clients themselves (with domain computer accounts) can update DNS records[46][47]. This prevents rogue devices from hijacking DNS names. The integration of DHCP with DNS ensures that forward (A) and reverse (PTR) DNS records stay in sync with the current IP allocations in the network[41]. For example, if a machine named PC123 gets a new IP via DHCP, DDNS updates mean PC123.corp.example.com will resolve to the new IP without an admin manually intervening. Name Resolution in Practice: Once DHCP has configured a host and updated DNS, other clients can resolve that host’s name to the correct IP via DNS. For instance, a printer comes online and gets IP 10.3.5.20 with hostname Printer7; DHCP updates DNS so that Printer7.corp.example.com = 10.3.5.20. When a user prints, their PC does a DNS lookup for Printer7 and gets 10.3.5.20, allowing it to connect. Similarly, reverse DNS is updated so if an admin does a PTR lookup on 10.3.5.20, it returns Printer7.corp.example.com. Forward vs Reverse Lookup Zones: Enterprises typically maintain forward lookup zones (hostname -> IP) for their domains and reverse lookup zones (IP -> hostname) for each subnet or block of addresses. Dynamic updates from DHCP often cover both: adding an A record in the forward zone and a PTR in the reverse zone[43]. Ensuring reverse DNS is populated can help with network management tools and some security software that performs reverse lookups. TTL and Scavenging: DNS records created via dynamic updates will have a time-to-live (TTL), often set to a relatively short value (e.g. 20 minutes by Windows DHCP)[48]. This means other DNS servers or clients cache them only for a limited time, reducing stale data if an IP changes quickly. Also, DNS servers can be set to scavenge stale dynamic records cleaning up records for devices that are no longer on the network (e.g. a DHCP lease expired and not renewed). This prevents the DNS database from bloating with outdated entries over time. It’s a best practice in enterprise DNS to enable scavenging for dynamically-updated zones to purge records that haven’t been refreshed in a long time (the DHCP server or client will refresh them periodically as long as the device is active)[49]. Service Discovery: Another intersection: DHCP can pass a DNS domain name (to set clients’ search suffix) and even specify DNS SRV records for services indirectly. For example, in AD, clients learn the AD domain name via DHCP option 15, then use DNS to find domain controllers (which publish SRV records in the DNS). Some networks also use DHCP to provide local DNS suffixes for different sites, etc., ensuring that when mobile clients move, they query the appropriate DNS domain.
In summary, DHCP and DNS in enterprises are often tightly coupled. DHCP ensures hosts have the correct DNS server info and informs DNS about hostnames/IPs, while DNS provides the name resolution that allows hosts to find each other and access resources by name rather than by numeric addresses. This synergy enables “plug-and-play” network access: a new machine can join the network and almost immediately be reachable by name and be able to reach others, without manual config.
Default Gateway: Assignment via DHCP and Role in Routing
Role of the Default Gateway: The default gateway is a crucial concept in IP networking. It is the router that a host uses to send traffic to destinations outside its own subnet. When a host wants to contact an IP that is not in its local network, it forwards those packets to its default gateway, which then routes them onward (hop-by-hop through the network or internet). In essence, the default gateway is the exit point from the local LAN[50]. Typically, the default gateway is a router or layer-3 switch interface that resides in the same subnet as the client (since a host can only directly reach gateways on its own subnet). For example, in 192.168.1.0/24 network, if the router’s interface is 192.168.1.1 and configured as the gateway, all devices will send off-subnet packets to 192.168.1.1. Without a correct default gateway, a host can communicate with neighbors on the same LAN (ARP can resolve those), but it will have no route to external networks, it cannot reach the internet or even other internal subnets. That’s why setting the gateway is a fundamental part of IP configuration.
Default Gateway via DHCP: DHCP automates the configuration of the default gateway on clients. As noted, DHCP Option 3 is defined for “Router” and is used to deliver one or more default gateway addresses to the client[18]. In most cases, a single gateway IP is given (though DHCP supports multiple in case one is preferred or for fallback). The DHCP server’s scope must be configured with the appropriate gateway for that subnet. For instance, for the subnet 10.5.0.0/24, the admin sets the scope’s “router” option to 10.5.0.1 (assuming .1 is the router’s IP). When a client on that subnet gets a lease, the DHCPACK includes “Default Gateway: 10.5.0.1”. The client’s OS will then create a default route in its IP routing table pointing to 10.5.0.1. Now any traffic destined for an address not in 10.5.0.0/24 will be sent to 10.5.0.1 for forwarding. This process is seamless and ensures hosts are correctly pointed to a router that can reach the rest of the network. It’s especially important in enterprises with many VLANs/subnets, each subnet will have its own gateway, and the DHCP scopes must supply the correct one. (A common mistake is misconfiguring the wrong gateway in a scope, leading to clients sending packets to a router that doesn’t serve that network.) The default gateway provided must be on the same subnet as the client’s IP. DHCP servers will usually validate that (for example, not offering a gateway that’s outside the leased IP’s network). If a host is configured with a gateway that is not reachable (different subnet or IP typo), the host will be unable to communicate off-network. Thus, correct gateway assignment is critical for connectivity.
Gateway in Routing: From the client’s perspective, the default gateway is just an IP address to send packets to. On the network side, that IP belongs to a router that has routing table entries to other networks. In an enterprise, default gateways often reside on core switches or routers that know how to route between all internal VLANs and also have a path to the internet (often via a firewall). When a client sends a packet to the gateway, the router will consult its routing table to forward the packet toward the destination (either to another internal subnet or out to the internet). For return traffic, the router does the opposite – it receives packets from outside destined to the client’s IP and delivers them (the router is often the ARP owner of the client’s network from outside perspectives).
Multiple Gateways and Redundancy: Normally a host has one default gateway. If that gateway goes down, connectivity is lost unless a new gateway is configured (some networks use dynamic routing protocols on hosts or clever tricks, but typical hosts rely on one gateway). Enterprises achieve gateway redundancy by techniques like HSRP/VRRP on routers (where two routers share a virtual IP as the gateway). From the DHCP side, the virtual IP is given as the default gateway. This way, if one router fails, the other takes over that IP and clients don’t need reconfiguration. DHCP can also be configured with multiple gateways (option 3 can list several IPs), but most OSes will only use the first as primary and others if the first is unreachable. So it’s more common to use a redundancy protocol at the gateway IP level.
Routing Outside Local Subnet: To illustrate the gateway’s role: say a PC at 10.1.1.50 (mask /24) wants to reach 10.1.2.75. The 10.1.2.0/24 network is different, so the PC’s TCP/IP stack says “destination not on my subnet, send to gateway 10.1.1.1.” It encapsulates the packet in a frame addressed to the MAC of 10.1.1.1 (obtained via ARP) and transmits. The router at 10.1.1.1 receives it, decapsulates to IP, sees destination 10.1.2.75. If the router has an interface on 10.1.2.0 or a route to it, it forwards the packet there (perhaps directly out interface 10.1.2.1). The destination host 10.1.2.75 then responds; its own gateway might be 10.1.2.1, so it sends reply to 10.1.2.1, which routes it back to 10.1.1.50. Without the gateway in this process, initial communication would fail. Thus, DHCP’s correct assignment of the default gateway ensures each host knows where to send non-local traffic[50][51]. In summary, the default gateway is the linchpin for off-subnet connectivity. DHCP handing out this info means administrators don’t have to manually set (or update) gateway addresses on each device, if the network’s router IP changes, updating the DHCP scope option updates it for all clients at next renewal. Clients can roam to different subnets and get the correct local gateway via DHCP. This is particularly useful in enterprises with many IP segments.
Enterprise-Level Configurations and Best Practices
Deploying DHCP and DNS in an enterprise involves additional considerations for reliability, security, and integration (particularly with Windows Active Directory or Cisco network gear). Below are specific configurations and best practices commonly seen at the enterprise level: DHCP on Windows Server (Active Directory Environment): Enterprises often run Microsoft DHCP and DNS servers integrated with Active Directory. Key points:
- Integration with AD DNS: Microsoft DNS (Active Directory-integrated zones) allows secure dynamic updates, meaning only authorized computers or DHCP servers can update DNS records[46]. Windows DHCP can be configured to perform DNS updates on behalf of clients. The DHCP server can be set to register A and PTR records for clients that can’t do it themselves[44][45]. A best practice is to enable “Always dynamically update DNS records” for DHCP and use an account with permissions for DNS updates (or configure DHCP to use the client’s provided FQDN and let secure updates occur with the client’s AD credentials). This keeps DNS in sync with DHCP leases while preventing unauthorized updates.
- DHCP Failover and Redundancy: Windows Server has built-in DHCP failover since Windows Server 2012. Admins can configure two DHCP servers in either hot-standby (one primary serving leases, secondary takes over if primary fails) or load-balancing mode (both serve leases, splitting the range, e.g. 50/50)[52][53]. This provides high availability, if one DHCP server goes down, clients can still obtain/renew leases from the partner. Best practice is to implement DHCP failover or at least the older “split scope” (e.g. one server serves 80% of range, another 20%) to ensure continuity of service.
- Avoid DHCP on Domain Controllers: Microsoft recommends not installing DHCP on a Domain Controller (if possible)[54]. This is for security and stability – Domain Controllers already run critical AD and DNS services. Keeping DHCP on a separate member server reduces risk (e.g., rebooting the DHCP server or vulnerabilities in DHCP won’t directly affect AD)[55][56]. However, in many small environments DHCP does co-exist on a DC; if so, careful attention to security (e.g. DHCP service runs with DC’s privileges) is needed[57].
- IP Address Management (IPAM): Large enterprises might use an IPAM solution (including Microsoft IPAM or third-party) to manage IP space, monitor DHCP/DNS, and avoid conflicts. This ties into tracking subnets and address usage.
- Lease Duration Tuning:Enterprises often adjust DHCP lease times based on subnet usage. For static office LANs, a longer lease (e.g. 8 days) is fine and reduces DHCP traffic. For guest networks or Wi-Fi with many transient devices, shorter leases (e.g. 1 day or a few hours) ensure addresses get recycled quickly. Striking the right balance prevents address exhaustion while minimizing the chance of conflicts. Many Windows DHCP best practices guides suggest monitoring utilization and adjusting lease length accordingly.
- Reservations: For devices that need a stable IP but are easier managed via DHCP, use DHCP reservations (mapping a specific MAC to a specific IP). This is often done for servers, printers, or legacy devices so you don’t have to configure static IP on the device, yet it effectively always gets the same address. Reservations are recorded in DHCP and are excluded from the dynamic pool.
- Rogue DHCP Protection: It’s important to ensure only authorized DHCP servers operate. An unauthorized (rogue) DHCP server can hand out incorrect IP settings (even a wrong default gateway or DNS, leading to man-in-middle attacks)[58]. Best practice is to use tools like DHCP Snooping on switches (for Cisco, etc.) to block DHCP replies from unknown sources, only ports leading to the official DHCP server are trusted. Also, Active Directory can be set to authorize DHCP servers (Windows DHCP won’t start offering in a domain environment unless authorized in AD, to prevent two Microsoft DHCP servers colliding).
- Cisco IOS and Network Devices:Cisco equipment often plays a role in DHCP/DNS at the network edge:
- DHCP Relay: In enterprise networks with multiple subnets or VLANs, you typically have central DHCP servers rather than one per subnet. Routers or Layer-3 switches on each subnet act as DHCP Relay Agents (Cisco IOS uses the ip helper-address command). The relay listens for DHCP broadcasts on a subnet and forwards them via unicast to the central DHCP server[59][60]. The server sees the relay’s source information (relay agent IP) to know which scope to use. The relay then delivers the DHCP replies back to the client[61]. This way, a single pair of DHCP servers can serve an entire enterprise network. Proper relay setup is a must-have best practice, ensure each VLAN interface has the correct helper-address pointing to your DHCP server IP(s). Without it, DHCP broadcasts won’t leave the subnet and clients on that subnet would fail to get leases[62].
- Cisco as DHCP Server: Cisco routers and switches can themselves be DHCP servers, useful in branch offices or simple networks. The IOS configuration involves defining a pool with the network and options (as shown earlier)[21]. This is suitable for smaller environments; in larger enterprises, Windows or dedicated DHCP appliances (like Infoblox) are more common for easier management and integration. But Cisco IOS DHCP is often used as backup (or for certain IoT VLANs, etc.). If using IOS DHCP, note features like show ip dhcp binding to list leases[63] and show ip dhcp pool to check scope usage[64].
- DNS Services on Cisco: Cisco devices are not typically authoritative DNS servers for enterprise domains, but they can be DNS clients (resolving names for logging, etc.) and can act as DNS forwarders/caches in some cases. For instance, Cisco has a feature where the router can forward DNS queries (set via ip name-server and allowing ip dns server to enable a simple DNS service). However, most enterprises rely on dedicated DNS servers (Windows or BIND on Linux). Cisco gear may host local DNS entries for minor uses (like an ISP router caching DNS for a small office). In enterprise exam context (e.g. CCNA), you should know how to configure a Cisco device to use DNS for name resolution (so you can ping by name from the router)[65], and that you can even configure a router as a basic DNS server for a small network.
- HSRP/VRRP Gateways: As mentioned, Cisco introduced Hot Standby Router Protocol (HSRP) to allow two routers to share a virtual IP for gateway redundancy. The DHCP scope in that subnet should hand out the virtual IP as the default gateway. That way, if the primary router fails, the secondary takes over without clients noticing a gateway change. For exam prep, remember that from the host’s view, the default gateway IP remains constant.
- General Best Practices:
- Use Multiple DNS Servers: Always have at least two DNS servers (primary and secondary) in an enterprise network. DHCP can be configured to hand out both IPs. This way, if one DNS is down, clients will retry the alternate. Ensure these DNS servers themselves have proper forwarders or root hints configured and replicate zone data (in AD-integrated DNS, all domain controllers running DNS have the copies of the AD zones).
- Time Synchronization: While not directly related to DNS/DHCP, ensure your servers (DHCP, DNS, DCs) have proper time sync (e.g., via NTP). AD domains require tight time sync for Kerberos. DHCP options can even supply NTP server info if needed (option 42).
- Documentation and IP Planning: Maintain clear IP addressing plans for all subnets and document what ranges are for static assignments versus DHCP. A common practice: assign static IPs (or DHCP reservations) to important infrastructure (servers, printers, network gear) outside the DHCP dynamic range[15]. For example, in a /24, use .1–.50 for static, .51–.254 for DHCP. This prevents accidental IP conflicts and makes it easy to identify devices by their address range. Utilize meaningful naming for DHCP scopes (e.g., “HQ-Floor1-10.10.1.0/24”) for clarity.
- Security for DNS: Secure your DNS: implement DNSSEC on external zones if applicable, limit zone transfers only to authorized secondary servers, and consider locking down dynamic update permissions. Also monitor DNS logs for suspicious lookups (some malware uses DNS tunnels or strange queries).
- Security for DHCP: As mentioned, use DHCP Snooping on switches to block untrusted DHCP offers[58]. DHCP Snooping also builds a binding table of IP-MAC, which can integrate with other security (like Dynamic ARP Inspection). On Windows DHCP, enable Conflict Detection (server pings an IP before leasing it, but use sparingly as it adds delay; it’s often off by default and can be enabled to 1-2 pings if IP conflicts have been an issue).
- DHCP Logging and Monitoring: Keep an eye on DHCP server logs – they will show when scopes are full or if there are many declines (which might indicate conflicts or rogue). Monitoring tools or even the built-in Windows DHCP statistics can alert you when a scope is low on free addresses. Plan to expand or split scopes before they exhaust.
- Backup and Recovery: Regularly backup DHCP and DNS configurations. Windows DHCP has an export function; DNS zone data in AD is in AD itself (backup your AD). In case of a server failure, have a plan, e.g., a standby DHCP server can quickly be authorized and take over (or use the failover feature). For DNS, AD replication usually covers redundancy if you have multiple DNS/DC servers.
- In summary, an enterprise deployment of DHCP and DNS should emphasize redundancy, proper network design (scopes matching subnets, correct gateways, etc.), and security. Windows Server and Cisco IOS each have roles to play: Windows servers often handle the higher-level name services and IP address management, while Cisco infrastructure ensures those services can be reached (via relay) and provides the packet-forwarding engine (routers for gateways). Following best practices such as DHCP failover, dynamic DNS updates, and security measures will lead to a robust, self-maintaining network where devices can join or move and remain reachable and properly configured with minimal manual intervention. Exam Tip: Remember the port numbers and message types (UDP 67/68 for DHCP[12], UDP/TCP 53 for DNS[40]; DHCP Discover/Offer/Request/Ack sequence; DNS A, AAAA, PTR, MX, etc.). Also be ready to explain the difference between iterative and recursive DNS queries[66], and how a default gateway works as the Layer 3 forwarding address for non-local traffic[50]. Knowing Cisco commands for DHCP (ip dhcp pool, ip helper-address) and the purpose of dynamic DNS in Windows are also common exam points. By understanding how DHCP and DNS complement each other, you can design and troubleshoot networks more effectively. For instance, diagnosing an issue where a client has an IP but can’t resolve names (DNS misconfigured) versus one where it can’t reach beyond the LAN (gateway missing or wrong). Use the synergy of DHCP and DNS to your advantage in enterprise network management.
References:
[1] [15] [16] [17] [21] [63] [64] Configure Cisco router as DHCP server https://study-ccna.com/configure-cisco-router-as-dhcp-server/ [2] [3] [20] The Backbone of Network Connectivity: How DHCP Simplifies Enterprise Management - Exam-Labs https://www.exam-labs.com/blog/the-backbone-of-network-connectivity-how-dhcp-simplifies-enterprise-management [4] [5] [8] [10] [11] [12] DHCP DORA Process Explained: Discover How It Works - SynchroNet https://synchronet.net/dhcp-dora/ [6] [7] [9] DHCP DORA process https://notes.networklessons.com/dhcp-dora-process [13] [14] [18] [19] [22] [23] [58] Dynamic Host Configuration Protocol - Wikipedia https://en.wikipedia.org/wiki/Dynamic_Host_Configuration_Protocol [24] [25] [26] What is Domain Name System (DNS) & How Does it Work? - Study CCNA https://study-ccna.com/domain-name-system-dns/ [27] [28] [34] [35] [36] [37] [40] [66] Recursive vs. iterative DNS queries: What's the difference? | TechTarget https://www.techtarget.com/searchnetworking/answer/Recursive-vs-iterative-DNS-queries-Whats-the-difference [29] [30] [31] [32] [33] [38] [39] What are DNS records? | Cloudflare https://www.cloudflare.com/learning/dns/dns-records/ [41] [42] [43] [44] [45] [46] [47] [48] [49] How to configure DNS dynamic updates in Windows Server - Windows Server | Microsoft Learn https://learn.microsoft.com/en-us/troubleshoot/windows-server/networking/configure-dns-dynamic-updates-windows-server-2003 [50] [51] IP Addresses, Subnet Masks, and Default Gateways https://www.networkcomputing.com/ip-subnetting/ip-addresses-subnet-masks-and-default-gateways [52] [53] [54] [55] [56] [57] Top 16 DHCP Best Practices: The Ultimate Guide - Active Directory Pro https://activedirectorypro.com/dhcp-best-practices/ [59] [60] [61] [62] DHCP Relay Agent - Study CCNA https://study-ccna.com/dhcp-relay-agent/ [65] Map hostnames to IP addresses https://study-ccna.com/map-hostnames-to-ip-addresses/